Why PoW is a Great Choice For New Layer 1 Blockchains
freezy gem
26 Sep 2022
•
19 min read
(..and Why Beanstalk is a PoW Chain)
Nowadays we keep hearing about new innovative Layer 1 projects coming out with consensus mechanisms being based off of alternatives to proof-of-work (PoW).
It seems like to be a new chain, PoS based consensus mechanism is a must, especially when almost every upcoming new layer 1 protocol is doing it (Near Protocol, Coda, Cosmos, Polkadot, Ethereum 2.0, and so on).
However, PoS is by far not a clear winner and comes with serious security concerns, unproven economics, and protocol complexity. Certain PoW based mechanisms on the other hand, oftentimes outperform PoS ones on metrics of decentralization and security.
This article will go over how to think about different mechanisms in terms of decentralization, security, and usability/scalability, and I'll break it up into 4 parts:
- Definitions
- How Decentralized Is It, Really?
- Security Vulnerabilities
- Usability & Scalability
Definitions
Terminology:
BFT: Byzantine Fault Tolerance is a property of consensus algorithms that states the system will always converge, or reach consensus, even if some participants are faulty or malicious. All successful consensus systems must exhibit this quality. Bitcoin and other Proof of Work (PoW) systems have proven to be probabilistically Byzantine fault tolerant.
PBFT: Practical Byzantime Fault Tolerance is an algorithm that describes specifically how to achieve Byzantine Fault Tolerance in the presence of malicious nodes. It states the system needs 3f + 1 nodes such that the system can handle up to f faulty nodes. Most Proof of Stake (PoS) protocols are PBFT-based.
(https://medium.com/s/story/lets-take-a-crack-at-understanding-distributed-consensus-dad23d0dc95)
ASIC: An ASIC (application-specific integrated circuit) refers to highly specialized hardware customized for particular use, like hashing the SHA256 hashing algorithm that Bitcoin uses. ASICs outperform commercial chips / machines for the specific task they are optimized for, and are generally cheaper for that task, making them an ideal choice for those wanting to mine cryptocurrency professionally.
Protocol Definitions:
Proof of Work (PoW) or “Nakamoto Consensus”: In Proof of Work systems, like in Bitcoin, miners hash the contents of the block they are proposing, and if the hash happens to contain the acceptable number of leading 0s, or be below some target number, that miner has found a valid block to propagate to the peer-to-peer network. This is why when you look at a Bitcoin block, like this one, the block hash contains several leading 0s. Since the hash cannot be predicted before hashing, it’s purely by chance that a miner might get an acceptable hash with enough leading 0s by dumbly hashing the block contents with a random number (nonce). However, you can increase your odds of finding a successful hash before anyone else in the network by adding more workers to try and guess that random number in parallel, and that’s exactly the purpose of mining pools. A mining pool is a service that orchestrates many machines joining together to try and find the appropriate hash for the block contents before anyone else.
In essence, PoW aims for 1 GPU = 1 vote. The more GPUs you have, the higher your chances of finding an acceptable hash and thus proposing a valid block to the network.
The consensus algorithm behind PoW systems is therefore to always pick the chain that is the “heaviest”, meaning one that has the most proof of work (in terms of valid hashes) behind it.
Examples: Bitcoin, Ethereum
Proof of Stake (PoS): Proof of stake is a system that requires capital (such as the native chain currency) instead of GPUs for network participation.
For PoS systems, the aim is to have 1 coin = 1 vote.
The more coins you have committed for the sole purpose of participation in the network, the higher your chances of winning the election to propose the next block. PoS’s signature characteristics are the concept of staking the coins you are using for participation such that the lockup period for them is significantly long even after you’ve proposed a valid block, and the concept of slashing a stake in the case that a miner is malicious and tries to propose an invalid block.
Note: Within PoS, there are variants, such as Bonded Proof of Stake (BPoS like Cosmos) and Liquid Proof of Stake (LPoS like Tezos). This is a great article that goes over the different PoS systems.
Examples: Tezos, Cosmos, Ethereum 2.0
Delegated Proof of Stake (DPoS): In delegated Proof of Stake, participants in the network do not get block reward proportional to their stake. Instead, participants in the network still stake their coins, but only for the right (proportional to their stake) to vote for a potential block producer. The top candidates by vote get to be the block producers, and they share the block reward evenly, while the stakers don’t get anything in return. For example, in EOS there are always only 21 block producers: the top 21 candidates by the number of votes they received from other stakers. In EOS, and in some other DPoS systems, the candidates who are in the top ~100 by popularity but who are not part of the 21 block producers, also get some daily reward for being stand-by block producers.
1 coin = 1 vote to elect a block producer who gets all the profit
Examples: EOS
Pure Proof of Stake™ (PPoS): This is a trademarked protocol system of Algorand. All network participants split the block reward evenly proportional to how much money they have in their wallets. In their own words, “Pure proof-of-stake means that for anyone wanting to participate in the Algorand network, they can signal that intent by flagging an account with algos as a participant (like flipping on a light switch). The likelihood of users being selected will be determined by the amount of algos they have in their account relative to all other accounts who have also signalled their intent to participate. “Pure” means they are free to come and go as they please as their algos are not locked up or “bonded” for any period of time as in other proof-of-stake systems. Any user can turn off the light switch at any time with no penalty or fear of losing their stake.” (https://www.algorand.com/what-we-do/faq/)
Examples: Algorand
Permissioned: While I will not go into depth what permissioned systems are and how they operate, it’s important to note which projects fall under that category. As the name implies, permissioned means that only certain entities are allowed to participate in the network as determined by the project creators. There are public and private permissioned chains. Public permissioned chains are ones that the public is allowed to transact with and observe, while private ones are completely closed off.
Examples: Ripple (and many others: https://arxiv.org/pdf/1905.05158.pd pg 10).
Other: The Stellar Consensus Protocol doesn’t really fall under any other category. Stellar Consensus Protocol is based on Federated Byzantine Agreement (FBA). “FBA provides an open membership service based on a trust model, where anyone can join the network, but only nodes trusted by others can be validators. More specifically, in FBA, each node selects a set of nodes that it trusts, which is called a quorum slice.“ (https://arxiv.org/pdf/1904.13302.pdf pg 1). In essence, nodes can pick their own quorums that they trust to reach consensus.
How Decentralized is it Really?
Centralized currency is controlled by the government that created it: the government has the power to dynamically inflate its own currency (see quantitative easing), the government has the power to censor how the money is used, or who can open a bank account. Centralized currency has plenty of merits, but can at times turn on its people with hyperinflation, hardships under authoritarian regimes, lack of privacy with massive data collection, or create major pain points moving money across borders.
Decentralized cryptocurrencies promise a strong alternative where no single entity or government controls the system. Its growth supply is completely deterministic and predictable by code, it does not censor who can and can’t use the system, and it is unbiased and unswayed by political events. The promise of a cryptocurrency is to be a border-less global autonomous medium of exchange. If crypto is aiming to be a strong alternative by being decentralized, then it better deliver on that promise.
Therefore, when evaluating a cryptocurrency, it is important to question how decentralized is it really as that is the core proposition for its existence.
Qualitative Observations about PoW vs PoS
When I asked various people in the crypto community, I received many qualitative opinions or remarks on whether or not PoW is better than PoS or vice versa.
Paraphrased Comments that are in favor of PoW (or against PoS)
PoW is better for decentralization because miners are forced to sell the coins they mine to continue operations, whereas that is not the same for PoS. - James Prestwich
Mining pools rely on hardware that breaks over time, forcing the top mining rig operators to either give up their hashpower advantage, or sell more of their coins to replace hardware. - James Prestwich
Moore’s law is dying, and therefore ASICs become less centralized over time because they have a longer lifetime. - Matt Corallo (TheBlueMatt)
Global wealth has been pretty centralized since ancient Mesopotamia. - Matt Corallo (TheBlueMatt)
"In the absolute best case, all that matters is how easy is it to regulate the biggest 1/3 of your consensus group" - Matt Corallo (TheBlueMatt)
“Basically the problem is that there is nothing stopping the initial parties from moving their stake around themselves to give the illusion that consensus decision have been distributed, but there isn't a good way to guarantee that the stake actually moved... Allowing first-movers with malice to maintain control forever if they like, biding their time to build confidence in a currency they have centralized control over” - Brandon Goodell (from Monero Research Lab)
If a mining rig has majority hash power on day one, it is not guaranteed for it to have majority hash power on day 100. Meaning that a player’s power distribution is uncertain over time. - James Prestwich
"Attack vectors are better understood for PoW" - [A lot of people]
In PoS there is no incentive for initial coin holders to distribute their coins, so you have the problem of the “rich get richer” scheme — Haseeb Qureshi, Howard Wu
If all of the miners were wiped out, they could all be replaced and the chain would go on. If all of the stakers would be wiped out, they could not be replaced as future stakers would need capital that is not available to them. — Bram Cohen
“Proof of Stake Sucks” — Bram Cohen
“At best, Proof of Stake is a decentralized centralized database rather than a decentralized decentralized database because of centralization around stake” - Bram Cohen
Paraphrased Comments that are in favor of PoS (or against PoW)
Decentralization is still a huge problem for PoW, so you cannot use that as an excuse for starting a new chain using PoW. While decentralization is still a problem for PoS as well, it has more upsides than PoW - Haseeb Qureshi
In countries where there is a crackdown on cryptocurrencies, it is much easier to detect (and raid or shutdown) PoW mining operations than PoS staking operations, therefore PoS leads to higher degree of decentralization because it’s harder to detect and shutdown — Kartik Talwar
Energy consumption — Howard Wu
Incentives for use of tokens – in PoS tokens can be used for voting or staking, whereas they just sit in your wallet without any further use for PoW chains. — Howard Wu
Cleaner on-chain voting or governance, and therefore cleaner path for upgrading or amending the protocol. Instead of looking at miners adopting the new software update and hoping that a significant majority of miners will upgrade in some allocated period of time, you instead have a baking period, a voting period, and a much cleaner upgradeability process. “you move everything to a software problem” — Howard Wu & Kartik Talwar
Subjective finality – there are some PoS algorithms that offer instant subjective finality, meaning that a transaction is guaranteed to be final and irreversible as soon as it is accepted on the blockchain, unless there is a major fork which is unlikely. (In contrast, for PoW chains, there is probabilistic finality, meaning that a user has to wait significant time after a transaction has been accepted on the blockchain to decrease its chances of being reversed by the network – more on that in the Usability & Scalability section below). — Howard Wu
Given capital, there’s less friction and operational cost in participating in staking than there is in mining. — Kartik Talwar
Quantitative Findings about these systems
Sometimes numbers speak louder than words, and we have enough quantitative information to judge blockchains by.
The research paper titled Impossibility of Full Decentralization in Permissionless Blockchains: by Yujin Kwon, Jian Liu, Minjeong Kim, Dawn Song, Yongdae Kim published in September 2019 took 100 top coinmarket cap coins, and did analysis on how decentralized they are. This paper looked at the past 10,000 blocks for PoW and PoS systems and 100,000 for DPoS systems before Oct 15, 2018 and made observations on how many unique block producers there were, and how evenly the wealth (meaning block rewards over time) was distributed amongst those block producers.
(All the following tables are using data taken out of the above mentioned paper)
- What is a Gini coefficient?
PoW Systems
| Coin name | Unique Block Producers | Gini coefficient |
|---|---|---|
Bitcoin |
62 | 0.8192 |
Ethereum |
65 | 0.8634 |
For Bitcoin, for the 10,000 observed blocks there were only 62 unique block producers. The wealth distribution for those 62 block producers had a Gini coefficient of around 82%, which is extremely unequal. From those 62 block producers,
4 block producers were responsible for producing 50% of the blocks!
For Ethereum, for the 10,000 observed blocks there were only 65 unique block producers. The wealth distribution for those 65 block producers had a Gini coefficient of around 86% (slightly worse than Bitcoin) and just 3 of those 65 unique block producers mined 50% of the blocks.
This can be attributed to mining pools which tend to centralize the hashpower for popular PoW systems.
PoS Systems
| Coin name | Unique Block Producers | Gini coefficient |
|---|---|---|
| Cardano | 7 | 0.0039 |
| Ethereum | 245 | 0.8391 |
Note: Cardano claims to be a PoS system but has literally not implemented its public consensus protocol and only has 7 permissioned nodes as of September 2019
The paper lists many PoS systems it looked at, like Cardano, Tezos, Qtum, Nano, Waves, and many others you probably have not heard of. Unfortunately, when you dig just a tad bit deeper into those projects, you’ll find that all of them (with the exception of Tezos), are either abandoned, vaporware, or not really PoS systems to begin with.
For example, Cardano, while technically a PoS, has literally not implemented its public consensus protocol and only has 7 permissioned nodes as of September 2019. Qtum appears to be based on Blackcoin’s consensus protocol which is closer to PPoS (and very questionable). Nano, although claims to be a PoS, is “built on a block lattice architecture, each account has its own blockchain as part of a larger directed acyclic graph” which is too far off to be in the same category. Waves launched as a LPoS (leased proof of stake) with a constant circulating supply which also is too different to be in the same category, and so on.
The only true PoS system that has launched and operated for over a year is Tezos. For their 10,000 observed blocks, there were 245 unique block producers (vs Bitcoin’s 62). The wealth distribution between those 245 block producers had a Gini coefficient of 84% (vs Bitcoin’s 82% – and remember that closer to 0 is better).
For PoS coins, there’s an analogous concept of staking pools when many participants pool resources to increase their chances of producing a block and sharing the reward. However, the staking pool industry is still highly undeveloped.
DPoS Systems
| Coin name | Unique Block Producers | Gini coefficient |
|---|---|---|
| EOS | 22 | 0.0447 |
Though they appear similar on the surface, there are big differences between DPoS and PoS systems. In DPoS, as a participant you vote for a block producer, and some top number of block producers by votes all share the block reward evenly, while the participants that voted them in get nothing.
EOS is a great example of a DPoS system. In EOS, there are 21 block producers. Out of the 100,000 observed EOS blocks, there were only 22 unique block producers (meaning that only one block producers was replaced in that time period). Its Gini coefficient for those 22 block producers is effectively 0 (~4%), meaning that those block producers did indeed split the block reward evenly.
However, It is very challenging to become a block producer today. At the time of writing, the top and 21st EOS block producer had 325,018,048 staked votes (where a 1 vote == 1 EOS) and 293,862,542 staked votes respectfully. At the time of writing, the price for EOS was $2.71, so to be a block producer it would take between ~$881M USD and ~$796M USD worth of committed and staked votes.
Security
In general, attacks on PoW systems are well understood, whereas the newer PoS systems have not yet been fully vetted in production systems. There are a variety of attack vectors that can target either system. Here, we will discuss only those attacks that are unique to either PoW or PoS.
PoW
51% Attack
The best known and most worrisome attack on PoW systems is the 51% attack. The 51% attack is far from being just theoretical, and we’ve scene many chains suffer from it:
- Ethereum Classic re-org
- Vertcoin’s tumultuous time of multiple re-orgs
- ZenCash’s 51% attack that was able to double spend $500k
- .. and so on
Having a hashing power dominance, which results in a 51% attack, can be attributed to ASICs, the highly specialized hardware made to efficiently run a particular hashing algorithm for a particular cryptocurrency. The response to mitigate such attacks is to make the protocol’s hashing algorithm be ASIC-resistant such that it’s harder to centralize hash power which allows one to execute such an attack. ASIC resistance has been a much discussed topic. Monero for example, schedules hard forks (or upgrades) to change its hashing algorithm every 6 months to prevent ASICs centralizing hash power. Despite criticism that Monero hasn’t fully achieved its goal and there is still centralization of hash power, Monero has never been successfully 51% attacked in its 5+ years of operation.
PoS
⅓ to stall, ⅔ to double spend
Generally speaking, for PoS chains, if ⅓ of the nodes that are participating in the quorum are faulty or unresponsive, then the network stalls; and if ⅔ of the nodes are malicious, then they’re able to to double spend or include an invalid block.
However, there’s an argument to be made that “In practice, no one will go out and start buying up tokens to attack PoS networks. It doesn’t make any sense. Putting aside that it is incredibly expensive, even for “small” networks”” (https://medium.com/@viktorbunin/proof-of-stakes-security-model-is-being-dramatically-misunderstood-4ed7b19ca419)
Grinding Attacks (“Nothing at Stake” problem)
Unlike in PoW systems, it doesn’t cost a PoS miner anything to build off of every possible fork choice. “It is computationally inexpensive to build on every fork because you no longer need PoW to create a block. Second, validators are expected to build on every fork because it is theorized that it is in their financial self-interest to do so. If validators mine on both (or more) chains, they will collect transaction fees on whichever fork ends up winning.” (https://medium.com/coinmonks/understanding-proof-of-stake-the-nothing-at-stake-theory-1f0d71bc027)
If every validator chooses to build off of every possible fork choice, then in PoS systems, it might cost as little as purchasing 1% of the stake in the network to execute an equivalent of a 51% attack ****on a PoW chain (https://github.com/ethereum/wiki/wiki/Problems#8-proof-of-stake).
Bram Cohen (creator of Bittorrent and founder of Chia, a Proof of Space protocol) has some pretty harsh words to say against PoS specifically in regards to this problem which leads to what he calls a “Grinding Attack” (https://www.youtube.com/watch?v=2Zlcgt8FVz4)
Long Range Attacks
I won’t explain in detail how exactly Long Range Attacks work (there are many excellent explainers like this one: https://blog.positive.com/rewriting-history-a-brief-introduction-to-long-range-attacks-54e473acdba9 or this one from Near Protocol with great visuals: https://nearprotocol.com/blog/long-range-attacks-and-a-new-fork-choice-rule/), just that this attack targets acquiring keys used to sign old blocks in the chain to rewrite chain history.
This, in my opinion, shows that there is an entire class of PoS attacks that PoW has never even had to consider. In PoW-based consensus systems, participants simply choose the heaviest chain that has the most hashpower (or work), put in to it. Rewriting history in PoW is computationally hard and expensive because subsequent blocks from the one that was changed need to be recomputed with appropriate proof of work. Since in PoS it is computationally inexpensive to produce blocks, instead of checking the work that was put in to produce that block, participants instead check the signatures of the quorum that produced that block. Changing history therefore becomes theoretically cheap because an attacker can buy the private keys from the quorum participants who signed a block long ago in the past and who have already gotten their stake back.
For a more formal explanation of Long Range attacks and Nothing at Stake problems, I recommend this paper (https://arxiv.org/abs/1809.06528) and it’s accompanying talk from BPASE ‘18 (https://www.youtube.com/watch?v=PGrWGMRbdvw) from researchers at Berkeley.
Long range attacks “can generally be solved with timestamping, but special corner cases do tend to appear in overcomplicated designs” (https://github.com/ethereum/wiki/wiki/Problems#8-proof-of-stake)
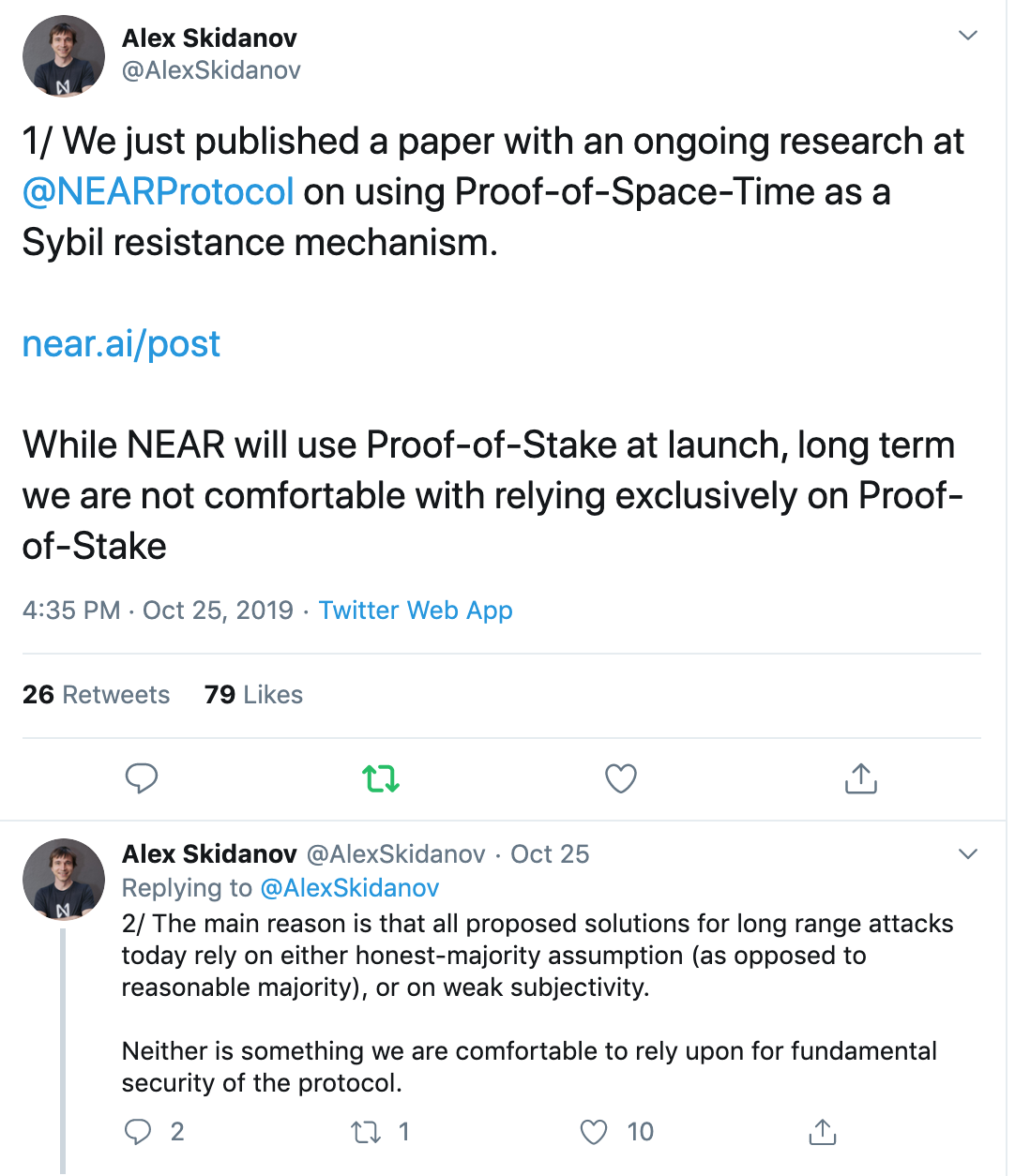
Near Protocol, working on one of the best industry solutions for a PoS based sharded blockchain, announced that they are “not comfortable with relying exclusively on Proof-of-Stake” for the main reason that the fundamental security of proposed solutions for long range attacks have weaknesses.
(https://twitter.com/AlexSkidanov/status/1187875251998191618)
While no system is perfect and both have actionable attack vectors, PoW systems have operated for over a decade and their attack vectors are better understood. In contrast, though it has not been successfully attacked, we have only seen one true PoS system launched and operated for longer than a year.
Usability & Scalability
Usability is a huge topic because despite Bitcoin’s global reach, there are only ~28M Bitcoin wallets in the world, and only about a quarter (~6.7M) have a balance of more than .001 Bitcoin (~$10) (https://bitinfocharts.com/top-100-richest-bitcoin-addresses.html).
There are many usability issues that can be solved with better design of user facing apps, but there are certain features that are simply limited by what the underlying protocol can do.
Difficulty of participation
Syncing a full node for any blockchain is a long process regardless of what consensus protocol is used.
There are solutions that both PoW and PoS systems could implement to speed up syncing of a full node, oftentimes even without a protocol change
- Snapshots (or Checkpoints)
- Ethereum (PoW): Ethereum’s Parity client has a Warp sync feature which takes a consensus based snapshot across Parity nodes at a 5k block interval (roughly 24 hours). When a new node comes online, it can download just that snapshot instead of the full blockchain history. (Ethereum state is still huge so this still takes a few days)
- Tezos (PoS): Tezos has a similar concept of “checkpoints”
- Zero-Knowledge Proof (ZKP) to validate a global state
- Coda aims to provide a proof at every block that the global state at that block is correct. It is like having a snapshot at every block with a strong guarantee that it is correct. Coda is working on a PoS chain (using Ouroboros) but this technique can be applied to many consensus protocols.
Scalability of transaction throughput
One of the most voiced concerns with blockchains is their limited transaction throughput. Visa can handle up to 65,000 transactions per second (https://usa.visa.com/dam/VCOM/download/corporate/media/visanet-technology/aboutvisafactsheet.pdf). Bitcoin can handle on average 4.6 transactions per second, Ethereum can handle about 15 transactions per second, and Tezos (a PoS system) can handle 40 transactions per second.
Cosmos / Tendermint
There are PoS systems that natively support a much higher throughput. Cosmos (based on the Tendermint consensus mechanism) operates by choosing the top 100 nodes ranked by how much funds they have staked to form a quorum of validators that chooses a leader to produce a block. Even though it is a PBFT based algorithm that has heavy communication overhead, they are able to achieve reasonably fast blocktimes because they limit the number of validators (currently) to at most 100. Cosmos is able to achieve roughly 6s block times giving it approximately 200 transactions per second. (When it was tested on 64 validators, it was shown to achieve 1000+ transactions per second.)
(https://www.preethikasireddy.com/posts/how-does-cosmos-work-part1)
There are others PoS based consensus systems like Polkadot’s GRANDPA + BABE hybrid and variations of Ouroboros being worked on, since none of those have shipped, there are no real metrics to report.
Generic Scaling Solutions
Sharding
- Sharding is the idea that instead of requiring every miner or full node on the network validating every transaction, you instead split, or shard, your miners in multiple groups so they can divide the load. If a protocol allows for 15 transactions per second, with 1024 shards you could then have 15 * 1024 transactions per second. The tricky part is making sure you don’t divide the security of your network by the number of shards. Cross-shard communication also needs to be seamless such that a user whose wallet is on one shard can easily send funds to a wallet that lives on a different shard.
- Generally speaking, sharding is only available for PoS chains because the protocol needs a way to assign different miners to shards in a balanced way.
Layer 2
- Layer 2 solutions include projects like Lightning, Plasma, Bolt, and many others
- Instead of having every transaction settled on chain, transactions between parties who anticipate to be trading often can be done off-chain, and then settled on-chain.
- Layer 2 approaches are available for both PoW and PoS systems
Finality
Often, the user has to wait for their transaction to not only be accepted by the network and added to a block, but for an adequate subsequent number of blocks to be added afterwards. This gives the user a stronger guarantee that the network won’t choose a different fork where their transaction wasn’t included. For Bitcoin, the rule of thumb is to wait for 6 confirmations, and at 10 min blocktimes, this means waiting for up to an hour to be sure your transaction really made it. For Ethereum, the rule of thumb is to wait for 30 confirmation, which is approximately ~7min. This is called probabilistic finality and all PoW chains share this characteristic.
The appeal of PoS systems is that since they are based on the PBFT algorithm, they can offer absolute finality. For example, in Cosmos/Tendermint, a block is final when the 100 validators verify and add it to the chain, therefore the transactions within that block are also finalized. This means that a user has to wait the ~6 seconds for a block with their transaction to be added to the chain, as opposed to 60 minutes with Bitcoin.
(https://medium.com/mechanism-labs/finality-in-blockchain-consensus-d1f83c120a9a)
Conclusion
No system is perfect, and both have serious trade-offs. To summarize:
PoS might seem like an appealing choice for new layer 1 protocols, especially when it feels like every new layer 1 protocol is doing it (Near Protocol, Coda, Cosmos, Polkadot, [Ethereum 2.0](https://www.ethereum.org/learn# eth-2-0), and so on), but it is by far not a clear winner as it comes with serious security vulnerability trade-offs and questionable economics.
On the other hand, PoW is a great choice for new upcoming chains as it is stable, battle tested, and at times outperforms PoS based chains on throughput (e.g. Ethereum’s 13s block time vs Tezos’s 1 min block time) and there are new layer 1 protocols planning to launch with PoW (such as Handshake and Beanstalk).
WorksHub
Jobs
Locations
Articles
Ground Floor, Verse Building, 18 Brunswick Place, London, N1 6DZ
108 E 16th Street, New York, NY 10003
Subscribe to our newsletter
Join over 111,000 others and get access to exclusive content, job opportunities and more!